DirectShow Spy is updated with a few new features:
- retroactive Intelligent Connect trace
- log output for IAMGraphBuilderCallback-related activity
- process name based black list to selectively exclude processes from spying
Intelligent Connect Trace
The utility received a capability to read back from its own log file (DirectShowSpy.log, located typically in C:\ProgramData directory) and reconstruct graph building sequence, including steps taken by DirectShow Intelligent Connect.
In order to activate the Intelligent Connect Trace property sheet, one needs to call exported function “DoGraphBuilderCallbackPropertySheetModal“, such as using runndll32 tool:
C:\DirectShowSpy>rundll32 DirectShowSpy.dll,DoGraphBuilderCallbackPropertySheetModal
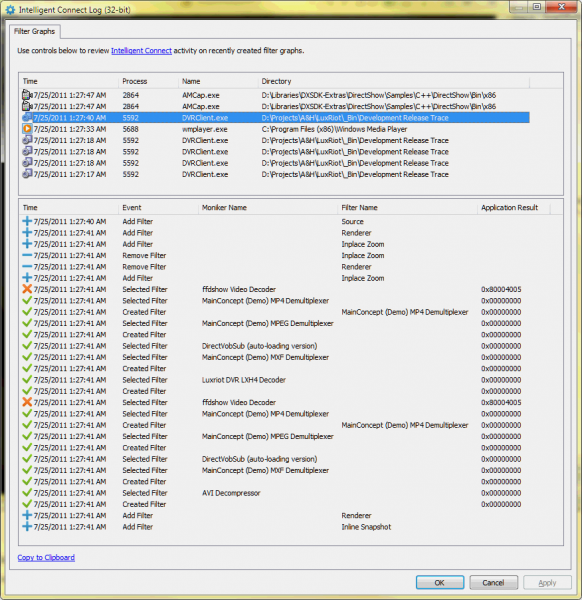
The upper part of the property page displays recently created DirectShow fitler graphs, newest to older. For a selected graph, the lower part displays events in chronological order. The events include:
- Adding a filter, at IFilterGraph2::AddFilter method
- Removing a filter, at IFilterGraph2::RemoveFilter method
- Selecting a filter, at Intelligent Connect’s callback at IAMGraphBuilderCallback::SelectedFilter
- Creating a filter, at IAMGraphBuilderCallback::CreatedFilter
The latter two methods also show “Application Result” column and values, which are HRESULT values returned by IAMGraphBuilderCallback callback provided by the application. Typically, a failure HRESULT code indicates that the application rejected the filter.
The trace log is good to expose all DirectShow junk installed in the system. For example,
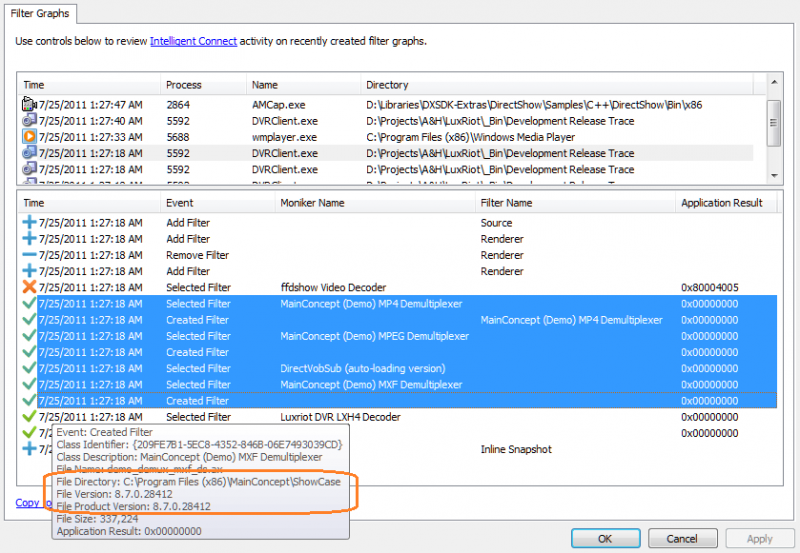
In an attempt to build graph to decode FourCC ‘LXH4’ video (which is a private alias for H.264 media type), Filter Graph Manager tried to apply ‘ffdshow Video Decoder’ filter, which is unable to process the feed, but is registered at an extremely high merit and violating the guidelines.
The tool shows that the file hosting the filter is “ffdshowBC.ax” and shows its location. The application however appears to be aware of this piece of trash, and returned E_FAIL (0x80004005) rejecting the filter.
How comes the garbage is hooking into place where it is not supposed to be, yet is sophisticated enough to reach such internals of operating system? This module is a clone/branch of well-known ffdshow software, which by default registers itself with abnormally high merit “with good intentions in mind”. A short-sighted manufacturer of cheap stuff IP camera duplicated the project, changed the GUIDs, packaged the pathetic crap into ActiveX control cabinet and started distributing it over clean and virgin workstations around the globe.
Going further with the the trace being checked, there are more things to enjoy:
Trying to decode the same H.264 video feed, the Filter Graph Manager mounting three demultiplexers made by MainConcept in a row, for MP4, MPEG and MXF containers. The utility immediately indicates that this trash contribution was brought by MainConcept Showcase 8.7.0.28412. One might wanted to install it for a purpose, and it started killing other DirectShow software it shares workstation with.
The good news is that the method is friendly for production environment and only requires to register spy and collect log file. You don’t eve need to check the UI at the same computer, it is possible to transfer the log file into development environment and have spy read the log there.
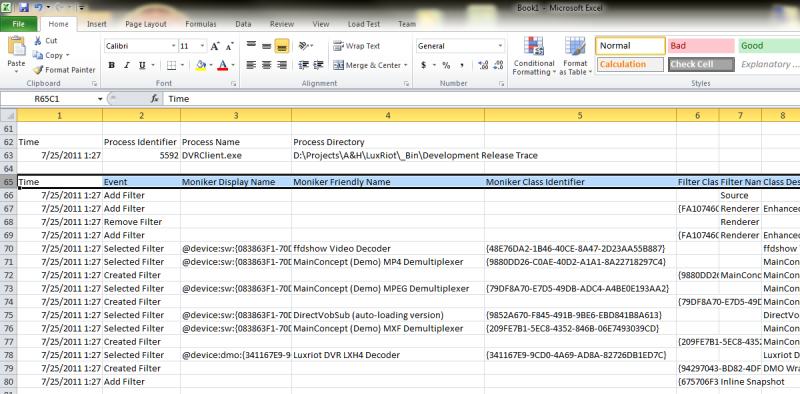
The “Copy to Clipboard” link is a convenient option to transfer the findings into tab-separated values format, such as to paste into Microsoft Excel:
Process Black Listing
The utility received a capability to selectively not load into specific processes. DirectShowSpy is a developer tool and is not intended for production environment, nor it is guaranteed to be issue-free. So in case of specific conflict it is possible to exclude specific process from applying a spy using registry:
The values are under HKLM, SOFTWARE\[Wow6432Node\]Alax.Info\Utilities\DirectShowSpy key, and there are three values defined:
- CFilterMapperSpy Black List – defines exclusion for filter mapper spying
- CSpy Black List – defines exclusion for filter graph spy (effective for most applications)
- CNoThreadSpy Black List – defines exclusion for filter graphs created with CLSID_FilterGraphNoThread
The exclusion value is a comma-separated list of process names, exact case-insensitive match for executable file names without directory and extension.
It is recommended that filter mapper spy has at least as rich exclusion list as the filter graph spy entires (otherwise, it is possible that spy might raise unexpected exceptions).
Partial Visual C++ .NET 2008 source code is available from SVN, release binary included (Win32, x64); installation instructions are in another post.