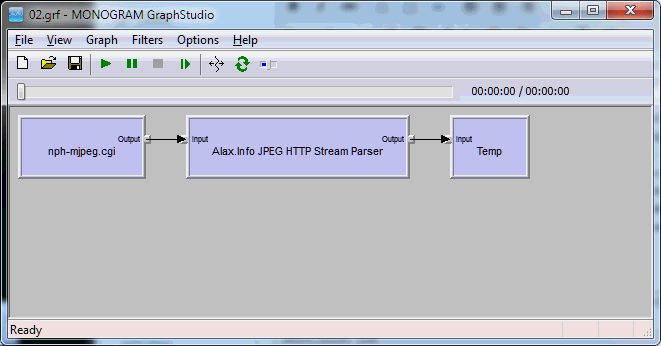
Microsoft Windows Virtual PC implements virtual machines and the application holds the entire machine state and virtual hard disk information in files. In a few large files in fact, so a question to move and/or backup the files is a question of periodic interest.
So what are the files it is using? First of all, the primary file a user clicks on to start virtual machine is a .VMCX file and it is located in “C:\Users\$(UserName)\Virtual Machines” directory. It is a shortcut to internal files and is holding very basic information about the machine, its state and location of other files.
<?xml version="1.0" encoding="UTF-16"?>
<!-- Microsoft Virtual Machine Description and Registration Settings -->
<vm_description>
<ram_size type="string">512 MB</ram_size>
<vmstate type="string">Hibernated</vmstate>
<primary_disk1 type="string">C:\Users\Roman\AppData\Local\Microsoft\Windows Virtual PC\Virtual Machines\Windows XP Mode.vhd</primary_disk1>
<secondary_disk1 type="string" />
<notes type="string">Windows XP Professional in "XP Mode"
Username XPMUser, Password XPM User</notes>
<vmc_path type="string">C:\Users\Roman\AppData\Local\Microsoft\Windows Virtual PC\Virtual Machines\Windows XP Mode.vmc</vmc_path>
</vm_description>
This directory has a special hidden desktop.ini file in it, which instruct the shell to treat the directory and the files in a special way, as Virtual PC files. This is also how Windows is providing user a link “Create virtual machine”.
The .VMCX file is editable (its format is based on XML) and it holds references to .VHD virtual disk files and .VMC virtual machine configuration files. However, .VMCX file is nothing but a shortcut only, and Windows Virtual PC will re-created those files once underlying .VMC file is double-clicked to be started, so there is no need to edit .VMCX files.
.VMC file is a virtual machine configuration file and it holds the settings a user provides for the virtual machine through settings dialog. The file is also using XML formatting, and is editable. While the file is small itself, its location is used as a base location for .VSV file, where software stores runtime state of virtual machine. The .VSV file size is stipulated by amount of RAM granted to the virtual machine, so the file may be pretty large itself and it might be desired to be moved to another location also. To achieve this, the small .VMC file needs to be moved to location of interest. A .VMC file can be double-clicked itself to start the virtual machine.

.VHD are the large files as they store data from virtual hard disks, so moving them may make sense. Additionally to the files themselves, if “Create Undo Disks” option is enabled, software will manage additional .VUD file with the name of format “VirtualPCUndo_$(VirtualMachineName)_$(Token).vud” file with changes that has not yet been applied. If moved, the .VUD files have to be thought of as a part of .VHD files.
By default a .VMC file holds both absolute and relative path refrences to .VHD and .VUD files, with relative reference as a priority. So if .VMC and .VHD (optionally with .VUD) files are moved together, no special path update/edit required. Software will be able to locate moved disk file automatically as soon as virtual machine is started. Still it is possible to edit the files manually and have files located in different directories. Also if disk file location is modified via GUI, software offers/attempts to strip undo disk .VUD file and cancel unapplied changes. If configuration file is edited manually, it is possible to keep undo disks without canceling the changes.
When moving files to a different location, make sure to check directory security so that Windows Virtual PC has sufficient privileges accessing files in the new location, or otherwise it would show ambiguous error messages “Could not register the virtual machine”.
See Also: Windows Virtual PC Tips on microsoft.com